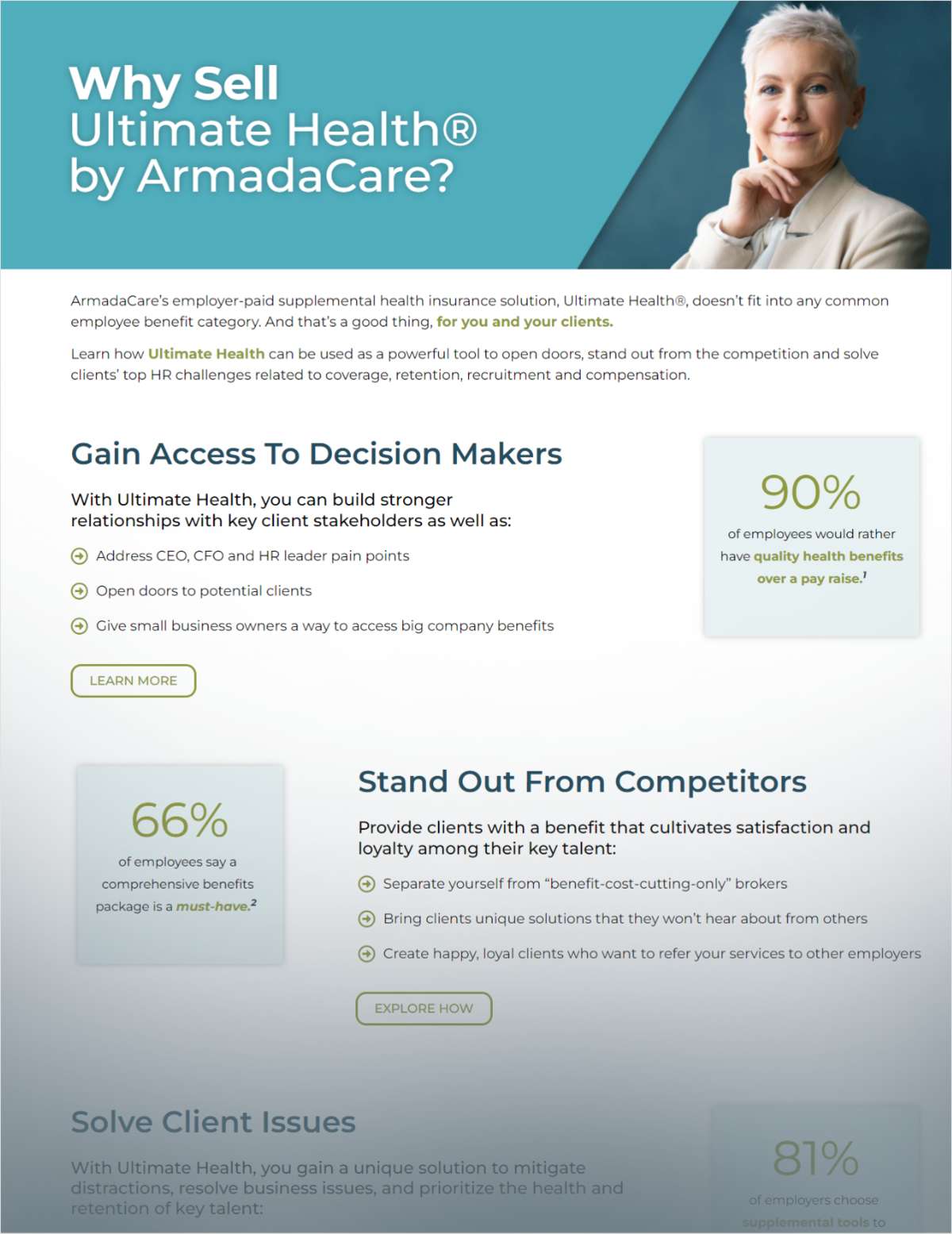
When the long-awaited federal and state health insuranceexchange websites launched Oct. 1, industry experts everywherepredicted an array of problems — slow loadtimes, inconvenient registration requirements and even site crashes— many of which came true. Now that the dust from theinitial pandemonium has settled, it's clear there’s one bigissue with the exchange sites few experts were able to predict:fraud.
|So far, most of the fraud has been of the information-gatheringvariety; consumers are directed to websites almost identical to thefederal or state exchange sites and instructed to enter basicinformation for registration. Some sites even ask consumers toenter financial information, such as credit card or bank accountnumbers, but according to experts, scammers will take whateverinformation they can get.
|“Scammers go after whatever personal data they can get,including Social Security numbers, credit card numbers, and, insome cases, even security questions and answers,” explains GregMancusi-Ungaro, chief marketing officer at BrandProtect, anorganization that provides corporations with tools to monitoronline activities that misuse or misappropriate corporatebrands.
|“People tend to choose the same security questions, and theclever scammer will ask those questions and then use thatinformation,” he says.
||“They really want to capture any personal data that will eitherallow them to directly access your bank accounts, or they are afterany information that will allow them access to your email account,”adds Dylan Sachs, director of identity theft at BrandProtect.
|“If you think about it, if a scammer has access to your email,they’ll now have access to all of your social media profiles,banking information, utilities information, and medicalinformation. Everything you do requires some kind of email address.If the criminal can capture your email, they can dig through yourarchives to find your bank account or even your Facebook usernameor password.”
|Also read: Target breach spurs ID theft insurance interest
|“They can reset your passwords to whatever they like, so thenthey have access to your entire friends network," Sachs says. "It’snot just the financial information; they want identity information,too.”
|With that information, Mancusi-Ungaro explains, scammers cancontrol your online identity and personalities.
|“Once they have that, there’s almost no limit to what they cando,” he says.
|As soon as the exchange sites launched, right alongside themwere fake websites that show up high in Google search rankings andlook official, so many consumers — especially older, less savvyseekers of health insurance — wouldn’t know that they’re enteringinformation on a fraudulent website. But Google isn’t the only waythat scammers have enticed consumers, notes Mancusi-Ungaro.
|“It’s fairly easy for a scammer to inundate email accounts withmessages that say ‘Only five days left! Click here to go directlyto the connector,’ or, ‘The exchange site is now up and runningsuccessfully. Click here to bypass the main login page and godirectly to choose your plan.’ In a time-pressured world whereeverybody’s talking about how the exchanges aren’t working, that’sa motivated message, and if it drives consumers to a site thatlooks appropriate, and they are seeing health plans, suddenly thedupe is done.”
|Sachs adds that because scammers tend to keep up with currentevents and the news, their strategies often take advantage ofconsumer confusion.
|“They leverage what makes the news, what the current events are,to prey on people’s vulnerabilities — and their fears andgenerosities, as well,” he says. “Whenever a natural disasterhappens that affects hundreds of thousands of people, all of asudden, you see these scam charities or fake Red Cross sitesappear, but the contributions are really just going to some badguy.”
|And the Patient Protection and Affordable Care Act is a primetarget because, as Mancusi-Ungaro notes, “the rollout in America isbasically an online event. Just like Cyber Monday is an onlineevent. Scammers anticipate when these online events willoccur — and when people are motivated to go online andcomplete a transaction, the scammers go crazy.”
|From a corporate perspective, companies whose brands are beingappropriated for scam purposes should be aware of where and howtheir brands are being used — because if a well-known corporatebrand is being used to perpetuate a scam, consumers are likely toblame the appropriated brand.
|“It’s incumbent upon large companies with valuable brands totake action to find and mitigate these online threats before theybecome serious business impediments,” Mancusi-Ungaro says.
|Sachs adds that brokers can help consumers by passing alonginformation to help identify a scam.
|“When you receive an email that expresses some type of urgency,anything that puts pressure on you, chances are its fake,” he says.“Always be suspicious if you are being pressured to do something.When in doubt, pick up the phone.”
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.