There are reports of data breaches in the newsevery week, impacting a range of organizations and industries.These cyberattacks are costing businesses, both large and small, agreat deal to resolve — from financial expenses to IT and legalresources to reputation recovery efforts.
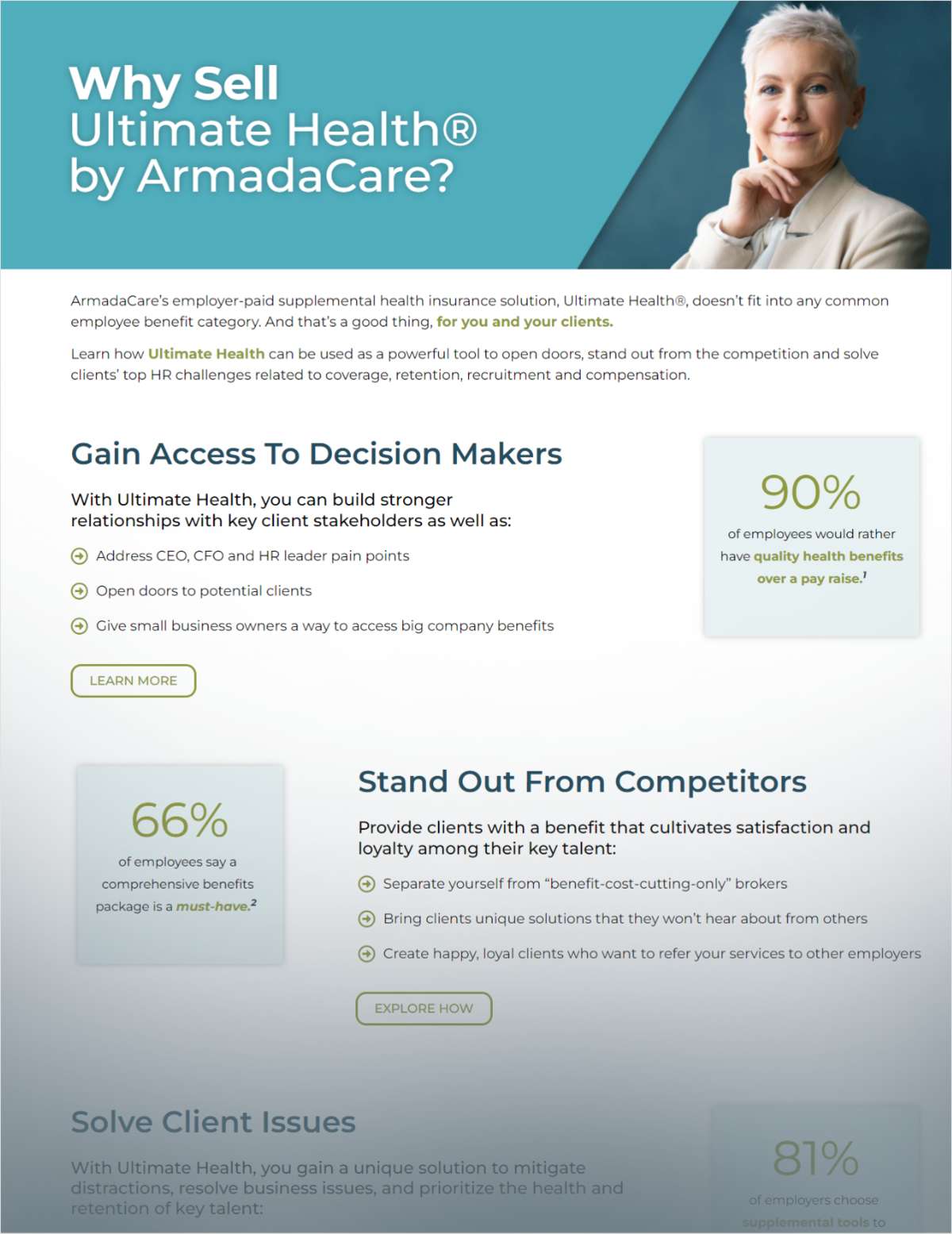
|According to a new study by the Ponemon Institute, data breachesare costing the health care industry $6.2 billion annually.
|Nearly 90 percent of health care organizations were victims of abreach in the last two years, raising concern for patients,employees, and others involved in the health care system.
|Today, the leading cause of health care data breaches aretargeted criminal attacks that seek to place valuable personalinformation into the hands of malicious actors.
|The personal information given out to health care organizationscan be some of the most valuable to cybercriminals. For example,when enrolling in benefits, the information submitted can includepatient names, family history, Social Security numbers, and billinginformation.
|It’s important to also note that not all breaches are malicious.Human error is often a cause of breaches, as CompTia’s International Trends in Cybersecurityreport found the 58 percent of security breaches are typicallydue to human error.
|So what can benefits administration technology providers do tokeep sensitive data secure from human error and malicious threats?
|
Conduct extensive user testing on your securitysystems
|Implementing user testing through a third party vendor allowsbenefits administration technology providers to discover gaps orholes in their security systems. This can be done via a usertesting group, which is comprised of individuals trained todiscover the predominant methods that cybercriminals would abuse tocompromise web-based applications.
|The group is given a platform with authorized access and fakescenarios, all set up to act as if the system was running as usual.As these experts go into the system and know what areas to try andhack, the organization is able to develop plans to combat or repairthese issues. User testing is similar to proofreading a paper;getting a second set of eyes on a program allows companies to seethe full risks of its security system.
|
Educate employees on cyberthreats
|As data breaches become a daily concern for IT departments,educating employees on the risks and dangers of cyberattacks becomes even moreof a priority. Benefits administration technology providers need toprioritize educational resources and programs to teach employeeshow to spot potential cyberattacks, especially as they are handlingtheir customers’ private information.
|An effective and simple way to train employees on how to spotstrange activity can be done via an email phishing awarenesscampaign. This involves delivering emails to employees with mockedup links or downloadable materials that, if real, would have thepotential to open users’ accounts up to cyberattacks. Organizationsshould also consistently remind its employees to report anysuspicious activity and to change their passwords regularly for amore secure system.
|
Automate processes to reduce the risk of humanerror
|Recently, Google was in the news for asuffered data breach via its benefits provider. Yet the reason forthis incident was human error, in which an email senderaccidentally sent a document to the wrong contact. Fortunately forGoogle, the damage was limited, but human error is not always soforgiving.
|With automation, benefits administration technology providershave the ability to decrease the chances of sensitive informationgetting into the wrong hands. This can be done by sending dummyfiles before sending the actual files to contacts. Another optionis to implement triggers on email accounts when certain informationis involved. For example, if a file is attached to the email,prompt the sender to confirm it is the correct file before sending.Implementing automation is a key factor in combatting human errorsthat could increase the risk of a cyberattack, especially when itcomes to personal data.
|
Beware of the insider threat
|While public perception is that these attacks result solely fromthe actions of malicious hackers outside of an organization,insider threats are a growing and serious concern. Vormetric’s 2015 Insider Threat Report reveals thatover 90 percent of U.S. organizations believe they are vulnerableto insider threats such as stolen passwords or email spam. In fact,the National Association of Manufacturers released a statement in April 2016 stating the theft oftrade secrets has cost businesses $250 billion per year.
|Benefits administration technology may want to go a step furtherto ensure employees are operating in the correct space. Requiringbackground checks and limiting access to sensitive data willprovide an extra level of security for patient, employee, andothers’ personal information.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.