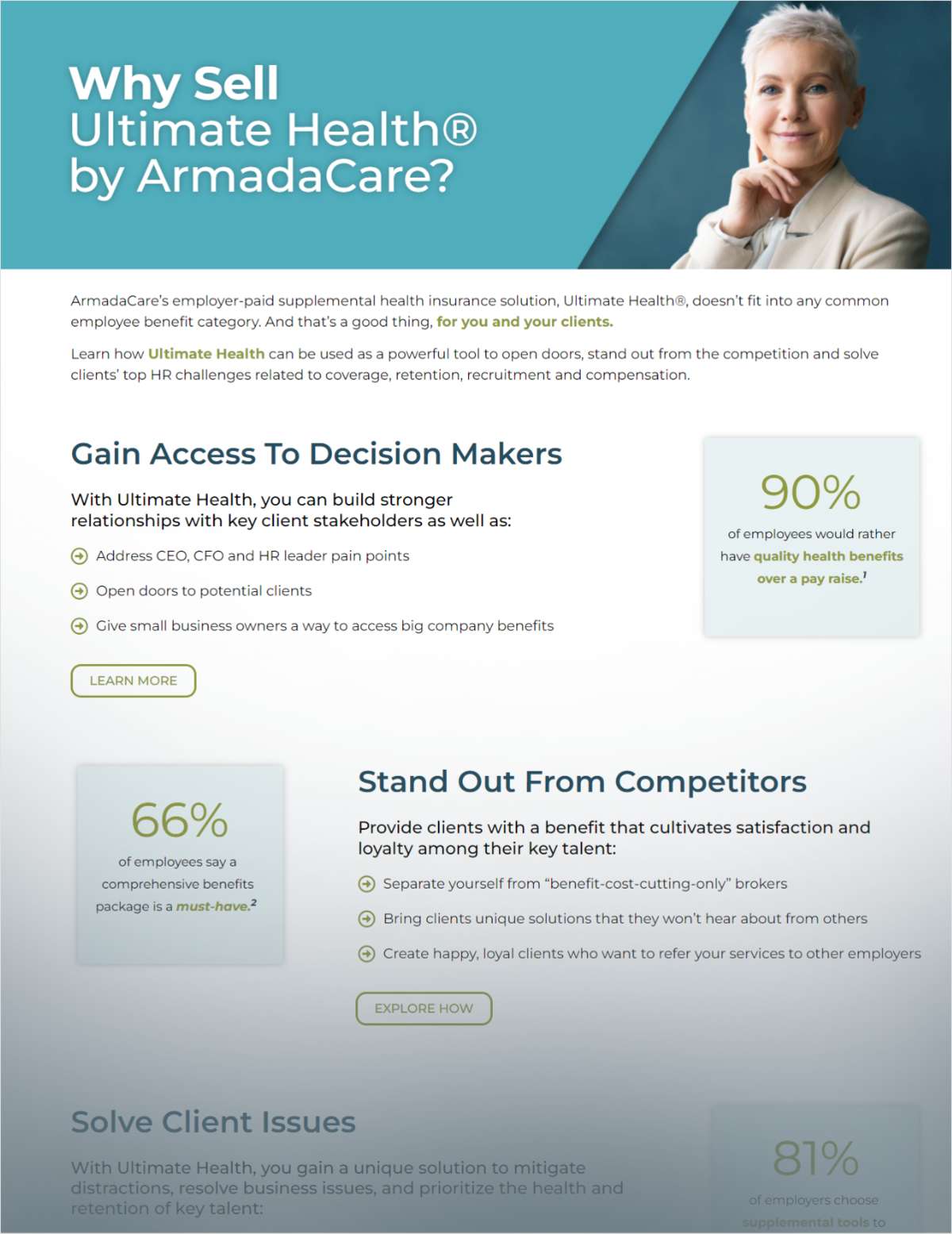
No business sector has been hit harder by cyberattacks than thehealth care industry, where companies work with private documents,proprietary medical records, and personal patient information on adaily basis.
|Related: Cybersecurity should be on plan sponsors'radar
|Health care companies, such as hospitals, pharmacies, andmedical facilities, fell victim to more cybercrimes than any otherindustry in 2015, according to IBM data.
|Last year alone, 100 million medical records were compromisedfrom more than 8,000 client devices in over 100 countries acrossthe globe, according to IBM.
|Data breaches haven’t just damaged the reputations of healthcare companies, but they have burned holes in their walletstoo.
|Cyberattacks now cost the U.S. health care industry $6.2 billionannually, according to the yearly analysis by the Ponemon Institute.
|Related: Ransomware is health care's newestchallenge
|These alarming statistics serve as a reminder for allorganizations to reevaluate their cybersecurity protocols.Regardless of your company’s cybersecurity budget, increasing yourprevention and protection measures can effectively detercybercrimes.
|Here are five primary strategies that every health care businessmust implement to fight this new epidemic haunting the industry.
|
Health care providers were the most targeted industry in2015 for cyberattacks according to IBM data. (Photo:iStock)
|1. Implement a cyber risk managementprogram
|The speed of technological change in the health care sector is rapid.The pace is simply too explosive for many hospitals and health careproviders to adapt to without external assistance. This, of course,requires money and operational support. Therefore, thedriving influence for a robust cyber risk management program mustcome from the board of directors.
|The Internet of Things (IoT) has tremendous application withinthe health care provider community, but it creates significantvulnerabilities as well. Help secure Protected Health Information(PHI) and other sensitive information by creating a risk managementinfrastructure based on advanced planning, education, training andmonitoring for the technological devices in question.
|IT managers, risk managers, in-house counsel and complianceofficers must be aligned in this area. Create a work group orcommittee comprised of key leaders in these disciplines to focus oncurrent and emerging issues. A budget for engaging with thirdparties to conduct vulnerability assessments, social engineeringreviews, penetration testing, employee training and education, andgeneral awareness surveys for their employees is essential.
|
Last year alone, over 100 million medical records werecompromised from more than 8,000 client devices in over 100countries across the globe. (Photo: iStock)
|2. Create a data breach response plan
|You cannot underestimate the importance of a plan, particularlya robust breach response plan, in the event of a loss ofinformation by breach, extortion, or employee error.
|Before creating a plan, know what’s at stake. Hackedorganizations can face fines and public scrutiny that can destroy areputation built on decades of trust. A breach can also lead tolost productivity in addition to lost revenue and the potentialexposure of confidential patient information. As seen in recentcases of ransomware, a type of virus that caninfiltrate a computer system and demand a ransom in exchange forcontrol of the system, the hospitals targeted were forced to revertto business continuity plans and IT down time procedures likemanual record keeping, scheduling and billing.
|Health care companies must have a response plan in place tomitigate these effects. Successful cybersecurity responsestrategies are all about repetitive training. Your primaryobjective when designing an incident response strategy is to createan actionable plan. Your strategy should account for places,employees and procedures, and should be applicable to multiplesituations.
|Be inclusive in your employee education and communication beforeand during your response. Include your software developers, callcenters, physicians, and other critical third parties in alltraining sessions.
|Your employees should also be trained on what actions they cantake to prevent a breach. For instance, they should be taught toidentify email scams and know when not to mix personal devices withwork tools.
|Social engineering or “deception fraud” is a commonly used and very simplemethod of tricking people into disclosing sensitive data likeSocial Security numbers. These confidence schemes use varioustechniques such as phishing and pretexting, impersonation that may result in financialloss. Companies of all sizes are targeted every day.
|
Since October 2009, there are nearly 1,600 cases ofhealth-related breaches impacting over 500 people. That’s almost195 annually for the past eight years. (Photo: iStock)
|3. Secure your technology
|With the expanding use of smartphones, gadgets, wearables, andmobile devices, it’s imperative to preemptively encrypt all of acompany’s mobile assets and allow remote wiping if the device islost or stolen. If employees transact business on mobile devices,companies should make sure they download high-tech mobile apps,such as GoodTechnology or IronBox Secure File Transfer, which canprovide a level of security for company devices.
|Any apps used by your company should come from a reputable firmand be thoroughly vetted by an in-house IT department.
|
The true number of actual breaches in health care and otherindustries could be much larger than what has been reported.Sometimes, breaches happen without raising any flags. (Photo:iStock)
|4. Know your risks
|It is important to note that there is no “off the shelf” policythat will address all risks. The hospital or health care providershould take the extra steps to first identify their current andemerging risks such as what devices and software solutions theycurrently use as well as those contemplated in the future. Next,they should create appropriate policies and procedures formitigating the inherent risks.
|Given the pace of technological change and the seemingly endlessnumber of bad actors that want health care data, it is essential tohire a third party to conduct a penetration test and attempt tohack into your system.
|This is a great way to find out if your company is effectivelyusing its security technologies. It will also allow you to see ifyour company is vulnerable and where your system may haveweaknesses. Have a third party conduct social engineering exercisesto test the weakest link in your security chain — your staff. Inthis case, a social engineering attack would involve trickingpeople into breaking normal security procedures by using a suddensense of urgency.
|Scammers, for example, will call the authorized employee withsome kind of urgent problem that requires immediate network access.To prevent this from happening, employees must remember to neverfeel rushed to give out confidential information by email or phone.Many scam artists will rush the process so that they can get whatthey need quickly without any background check.
|Human error is the leading cause of creating openings forhackers to leverage. A thorough IT vulnerability assessment canhelp you understand whether your security policies and awarenessprograms will actually prevent outsiders from obtaining valuableinformation or confidential patient data directly from youremployees.
|
According to the 2013 Ponemon “Cost of a Data Breach”report, mediating a breach costs in the range of $233 per comprisedhealth record. (Photo: iStock)
|5. Create a customized insurance policy
|The best way to ensure your assets are protected is to create acustomized insurance response and make sure it’s well communicatedthroughout the enterprise. Cyber liability insurance is notstandard and can come with procedure requirements and significantexclusions. Knowing your insurance will help avoid claim denials.Hold a detailed planning session with risk management, IT, seniorleadership and your risk advisors, perhaps as a part of yourenterprise risk management (ERM) process, to determine the specificprotections your organization needs.
|This approach must be continually deployed as new technologies,such as BYOD (bring your own device) and wearables, hit the healthcare industry.
|Hospital risk managers and clinicians are familiar with the“plan, do, check, act” approach to risk management. These samebasic concepts apply when creating the right insurance plan. Ifmaking the organization look less attractive to the “bad guys”prevents one intrusion, hack or ransom, the investment of time andmoney will be time well spent.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.