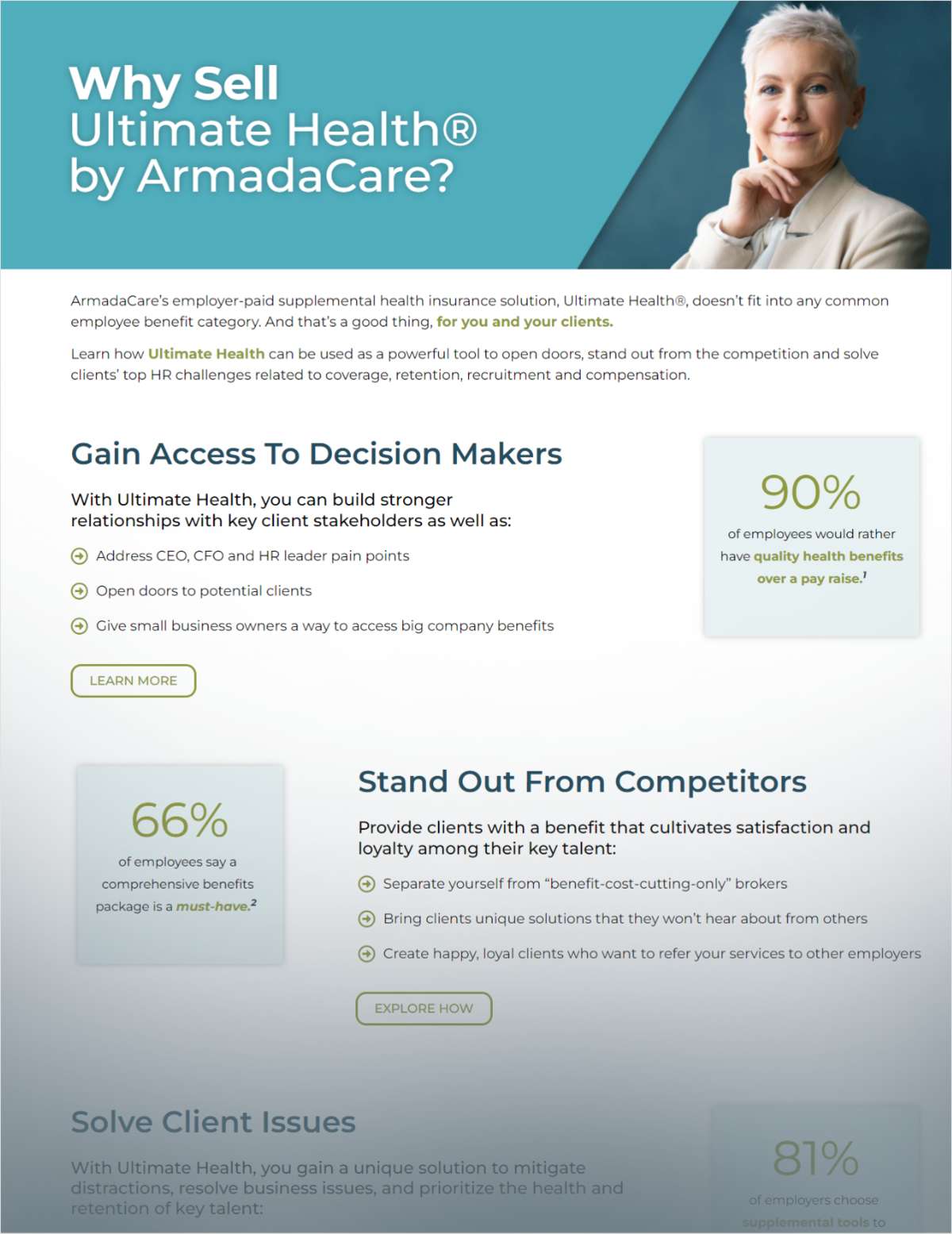
Companies looking to mitigate their risk through cyberinsurancebe forewarned—selecting and purchasing a policy may be the easypart. Like many insurance policies, however, cyberinsurance cancome with many caveats, and the devil is in the details.
|Related: Many businesses unprepared for cyberattacks
|For Judy Selby, consulting managing director at BDO andmoderator of the upcoming "You Finally Bought the CyberinsurancePolicy, Now What?" panel at CyberSecure, there is a pressingneed for greater awareness of what cyber coverage reallyentails.
|Related: Good news and bad news on health carehackings
|Selby noted that her panel will be focused on how companies canensure the coverage they have will actually help when a securityincident occurs. "We want to increase awareness of some of theobligations that are placed on the policyholder in connection withmany cyberinsurance policies that are on the market."
|Related: Cybersecurity concern increasing forretirement plan participant data
|In the current market, there's no standardization tocyberinsurance policies, Selby said, but underlying them are somecommon themes. With this in mind, policyholders can take certainsteps to maximize coverage in the event of a breach.
|The worst position a company can be in, she added, "is if theyactually go through the process of obtaining cyber coverage, andthey are not aware of certain obligations in the policy, and theydon't fulfill those obligations. And then coverage is jeopardizedbecause of that."
|But what do some of these obligations entail?
|For one, a company has to make sure it is completely upfront andhonest with a cyberinsurance provider about how they manage andsecure their data in-house.
|"If during the application process [companies] make certainrepresentations about how they treat their data and if thoserepresentations are in fact not true and an incident arises becauseof that, the insurance companies can then look back at therepresentations and question whether the coverage should beimpacted," Selby cautioned.
||But she also noted that some insurance providers limit theirexposure to such an event by requiring an insured company to employ"reasonable [cybersecurity] measures." At times, however, thesespecific measures can be negotiated.
|Related: Hackers said to be eyeing $5 trillion401(k) market
|Obtaining cyberinsurance also adds the obligation of immediatelyinforming insurers when a breach occurs—an easily overlookedresponsibility that could prove costly to forget.
|Selby explained that "like other insurance policies,cyberinsurance policies contain provisions that address how youprovide notice of a claim or potential claim. … Many insurancepolicies will say that you can't incur any costs before you providenotice to us, so any costs you incur have to be with the insurancecompanies' consent."
|However, "in breach situation where everybody's hair is on fire,if they don't have a practiced incidents response plan it may notbe top of mind to place a call to put the insurance company onnotice," she said.
|And far from just being one step in an incident response plan,cyberinsurance policies will likely also govern who else iscontacted in the post-breach response. Many policies, Selby said,"have identified certain firms that [insured companies] arerequired to deal in the event of a breach. For example they have aplan set up for a certain number of law firms, a certain number offorensic firms, etc."
|Despite cyberinsurance's broad influence over a company'scybersecurity plans, however, coveragecan lapse, should a company go through a restructure, such as thosebrought on by mergers or acquisitions.
|How cyberinsurance is affected by such restructures may dependon a multitude of factors, such as "the size of the target company,as compared with the acquiring company," Selby said. "There's a lotof hoops companies need to jump through in connection with mergerand acquisition situations in order to extend coverage."
|The complexities managing a cyberinsurance policy are unlikelyto end with just those few obligations. Selby noted that, ascyberinsurance usage grows over the next few years, she expectscyber-insurers to be "very innovative in trying to come up with newproducts to address an emerging risk and to provide coverage fordifferent types of injuries that can arise from breachsituations."
|"It will be interesting to watch how it all develops," shesaid.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.