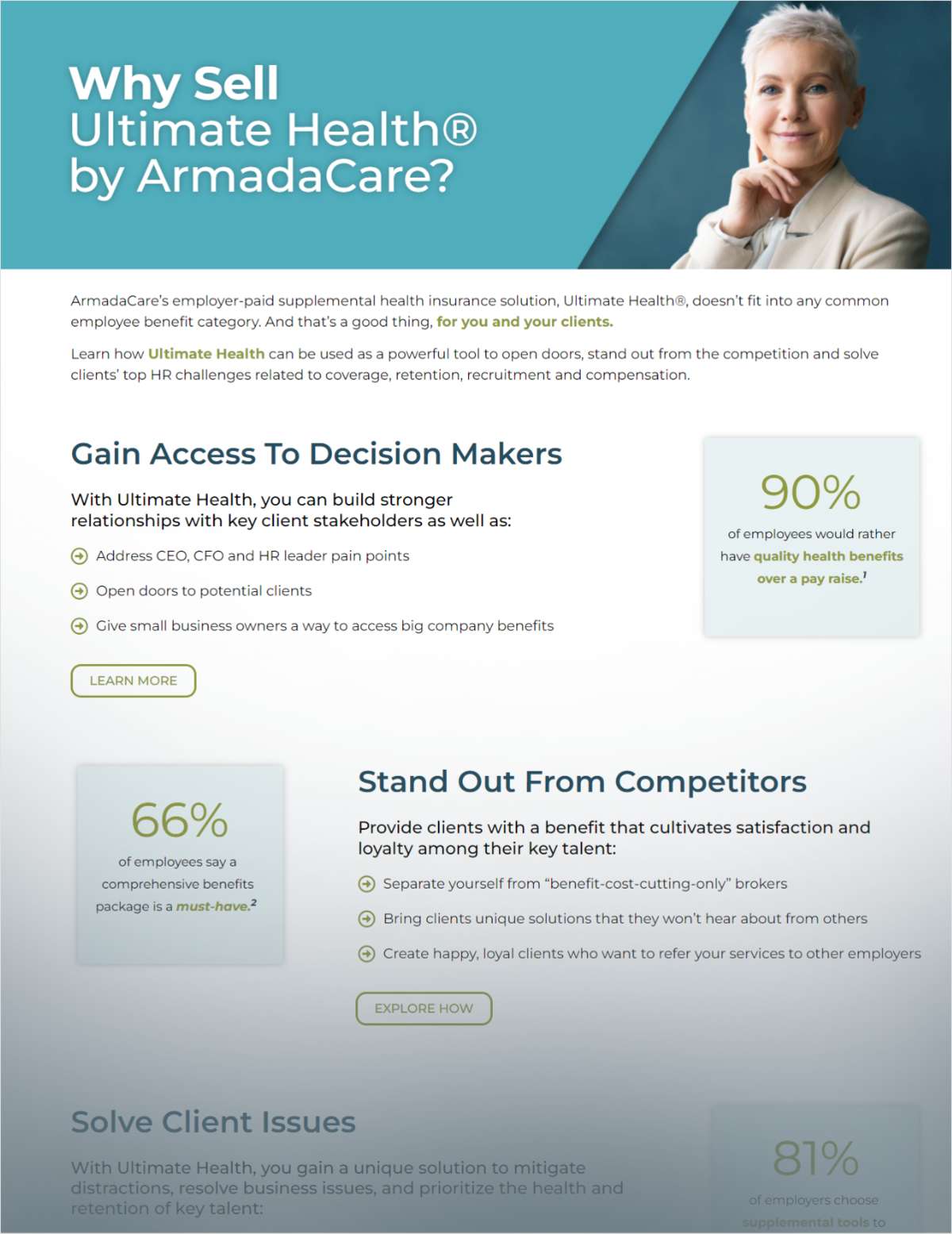
(Bloomberg) -- Extortionist hackers who may be using leakedcomputer exploits from the U.S. National Security Agencyinfiltrated computers in dozens of countries in a fast-spreadingcyber attack that forced British hospitals toturn away patients and breached systems at Spain’s Telefonica SAand organizations from Russia to Taiwan.
|The ransomware used in Friday’s cyber attacks encrypts files and demands thatvictims pay $300 in bitcoin for them to be decrypted, the latest ina vexing style of security breaches that, at the very least,forces organizations to revert to backup systems to keep criticalsystems running.
|Related: 3 ways financial firms fail at cybersecurity
|The malicious software has infected more than 75,000 computersin 99 countries worldwide on Friday, most of them concentrated inRussia, Ukraine and Taiwan, according to Dutch cybersecuritycompany Avast Software BV.
|Security researchers at defense contractor BAE Systems said theattackers were using a vulnerability that has been patched,but attackers often take advantage of the fact that manyorganizations and individuals don’t routinely update theircomputers to fix security issues.
|Some security researchers said the exploit in the MicrosoftCorp. system was published by the Shadow Brokers, a group that hasbeen leaking stolen hacking tools purportedly from the NSA.
|Sixteen NHS organizations were hit in the U.K. on Friday, whilea large number of Spanish companies were also attacked usingransomware. In the U.K., hospitals urged people with non-emergencyconditions to stay away after the cyber-attack affected large partsof the country’s National Health Service.
|Related: 10 ways small businesses can fight cybercrime
|“The NHS has experienced a major cyber-attack, we are workingwith law enforcement and our advice will follow shortly!” ActionFraud, the U.K.’s central cyber-crime unit said on Twitter. TheNational Cyber Security Center said: “We are aware of cyberincident and we are working with NHS Digital and the National CrimeAgency to investigate.”
||Hospitals in London, North West England and Central England haveall been affected, according to the BBC. Mid-Essex ClinicalCommissioning Group, which runs hospitals and ambulances in an areaeast of London, said on Twitter that it had “an IT issue affectingsome NHS computer systems,” adding “Please do not attend AccidentAnd Emergency unless it’s an emergency!”
|The impact on services is not due to the ransomware itself, butdue to NHS Trusts shutting down systems to prevent it fromspreading, said Brian Lord, a former deputy director of GovernmentCommunications Headquarters (GCHQ), the U.K.’s signals intelligenceagency, who is now managing director of cybersecurity firm PGICyber. Lord, who described an attack of this type as "inevitable,"said the impact was exacerbated because most NHS Trusts had "a poorunderstanding of network configuration meaning everything has toshut down."
|A screen-shot of an apparent ransom message, sent to a hospital,showed a demand for $300 in bitcoin for files that had beenencrypted to be decrypted.
|Workers across the NHS have since been sent emailsfrom the health service’s IT teams warning not to open or clickon suspicious attachments or links.
|Spain’s National Cryptologic Center, which is part of thecountry’s intelligence agency, said on its website that there hadbeen a “massive ransomware attack” against a big number of Spanishorganizations affecting Microsoft Corp.’s Windows operating system.El Mundo reported that the attackers sought a ransom inbitcoin.
|“We’re aware of reports and are looking into the situation,”said a Microsoft spokesman.
|Ransomware typically gets onto a computer whena person unsuspectingly downloads a file that looks like a normalattachment or web link. A hacker can then trigger the malware tofreeze the computer, prompting a person to pay a ransom or lose alltheir files.
|Hospitals have been a common target because theculprits know how critical digital records are for treatingpatients. There have been several incidents in the U.S., includingone in Indiana where a hospital’s IT system was taken down andpatients had to be diverted to other facilities, according to alocal news report.
|Ransomware attacks have also been soaring. The number of suchattacks increased 50 percent in 2016, according to an April reportfrom Verizon Communications Inc. These types of attacks account for72 percent of all the malware incidents involving the health-careindustry in 2016, according to Verizon.
|"The large-scale cyber-attack on our NHS today is a huge wake-upcall," said Jamie Graves, chief executive officer of cybersecuritycompany ZoneFox.
|Andrew Barratt, managing principal of Coalfire, a company whichprovides cybersecurity risk assessments to the health-care sector,said that many NHS hospitals used personal computers with outdatedWindows-based operating systems, which have makes them easy toattack. He said many of these systems were too old to patch andthat many NHS Trusts did not spend enough time on technical bestpractices and audits, leaving them vulnerable to a variety ofpotential cyber-attacks, including ransomware.
|Copyright 2018 Bloomberg. All rightsreserved. This material may not be published, broadcast, rewritten,or redistributed.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.