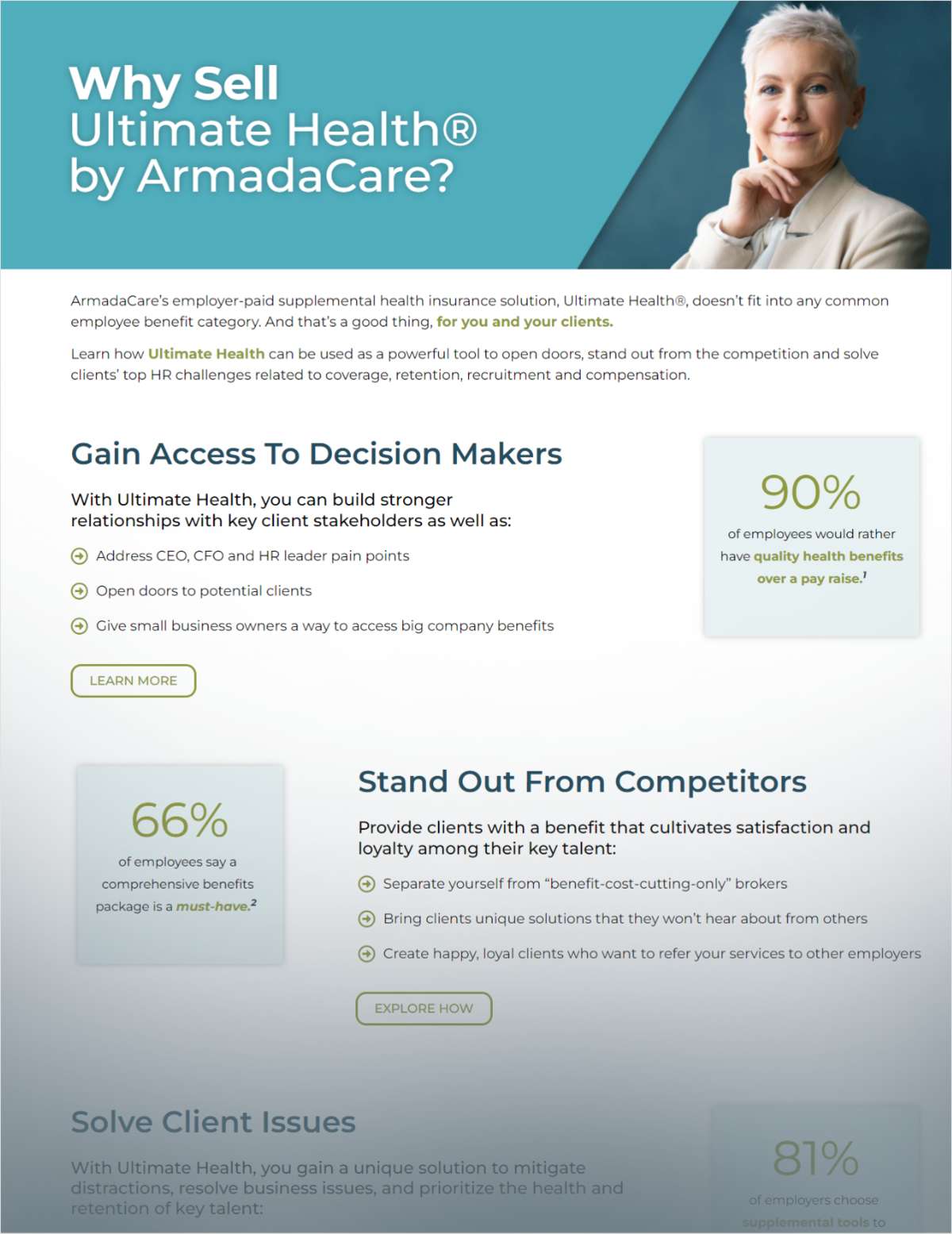
Ransomware attacks continue to plaguebusinesses large and small. With impacts on all kinds oforganizations — from independent consultants to leading health careproviders, colleges to online gaming sites — employers must bealert to the dangers of ransomware.
|But before companies can devise an effective strategy to thwartthe hackers, it’s important to first understand whata ransomware attack looks like, how itbegins and what kind of damage it can do.
|What does a ransomware attack look like?
The delivery of ransomware is simple enough. Mostinstances start with a phishing attack, where a user receives ane-mail containing an unsafe link or a corrupted file or executableattachment.
|Many employees and contractors haven’t been trained to spotsuspicious activity and are unaware of the potential risksassociated with these untrusted messages — a fact the hackers counton to carry out their plans. Rather than taking a few steps toverify the e-mail’s authenticity, the employee opens the file orclicks on the web link, and a ransomware attack is born.
|The ransomware infection immediately gets to work blockingaccess to data on the user’s computer. In many cases, it spreadsthroughout the network to other locations, such as connectedcomputers, the company’s servers and any cloud-based storagerepositories.
|This proliferation across the network is rapid, typicallyhappening much too quickly for the organization to effectivelyblock or delete the ransomware before it inflicts harm. A screensoon appears, warning the user that they can no longer accessanything on their computer unless they pay the ransom to get theirdata back.
|Damage from the ransomware attack becomes all too real as theinfection encrypts data files and prevents access to theinformation inside. Files may also be renamed using unrecognizedfile extensions, such as “.zzz” or “.OMG!” to highlight the factthat they cannot be opened.
|Further destruction occurs when the ransomware deletes shadowfiles, effectively eliminating the possibility of accessing localbackups that were previously assumed to be safe.
|What can be done?
An infected business has few options once ransomware infiltratesthe network. One option is to pay the ransom and hope data accessis restored. It’s hardly a foolproof strategy. Sometimes thecriminals simply take the money and run, leaving the organizationin dire straits and lighter on cash.
|Another option is to find a safe computer — one that wasn’tconnected to the network when the ransomware took over — andretrieve backup data from an isolated hard drive or other externallocation that was not affected.
|A third alternative is to wipe the entire network clean or startfrom scratch with new equipment, rebuilding the datasets fromprotected archives and memory. Each strategy has its shortcomingsand all will cost the company in time and money.
|There may also be a significant delay as the organizationattempts to return to normal operations with incomplete data orincapacitated hardware. No matter which route the business takes,sensitive information — possibly including corporate financials andemployees’ personal data — has been compromised by the attack.
|Rock-solid preparation is key
The best approach is to develop a plan to protect theorganization from a ransomware attack long before one occurs. Aproactive strategy is the first and best line of defense againstthe harm that employees, the business and its customers could faceif ransomware is allowed to enter the network.
|HR managers are in a good position to help shape that plan andguide its adoption within the organization.
|Begin by collaborating with the IT group to create a backup andrecovery strategy that is impervious to ransomware. Archival copiesof confidential and business-critical data stored in an unconnectedlocation — either onsite or in the cloud — will provide a safe wayto restore information and continue operations.
|The type and volume of data that must be protected within the HRorganization should be discussed as part of the master plan,including not just employees’ personal information but also datarelated to contractors, candidates and board members.
|Developing company-wide awareness is another important componentin a ransomware protection plan. When most organizations think“awareness,” they think annual training in a classroom room, butthe best awareness programs go beyond the classroom.
|Tools such as white-hat phishing tests can be used to evaluatethe effectiveness of existing security measures. HR managers areexperts at disseminating training elements to the employee base —for instance, through eye-catching e-mails to confirm they know howto spot suspicious messages.
|In addition, by disseminating regular reports to employees aboutreal-world ransomware cases and other cyber security threats, theHR team can inform employees about which types of attacks aretrending.
|The company newsletter and intranet site can be used to spreadthis information across the workforce. An awareness program’s reachcan also be extended by establishing and teaching e-mail rulesbuilt around good security practices. These may include movinge-mails with attachments to a quarantine location or into the junkmail bin.
|Employers who are serious about avoiding the risks of ransomwarewill also want to explore next-generation anti-malware tools.Leading solutions can “inoculate” servers and hosts againstransomware by recognizing the apps that are being used in theattack and defeating them, a security approach designed to shieldthe organization from the ravages of an attack.
|Many top-tier offerings can also identify suspicious e-mailattachments and either block users’ ability to open or launch them,or move them to a network location that can’t be used as an entrypoint to the rest of the firm’s data. If in-house technology andexpertise isn’t available, there are subscription-based servicesthat grade the safety of the sources of incoming e-mails.
|When looking at the landscape of ransomware, it’s clear that anemployer’s best defense is rock-solid preparation. These attackstypically can’t be reversed, and making matters more difficult isthe energy that criminals are putting into devising new deliverymethods to stay one step ahead of their victims.
|But with a strong focus on employee training and awareness, HRmanagers can play a key role in creating a privacy culture thatbuilds best practices into everyone’s day-to-day behavior.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.