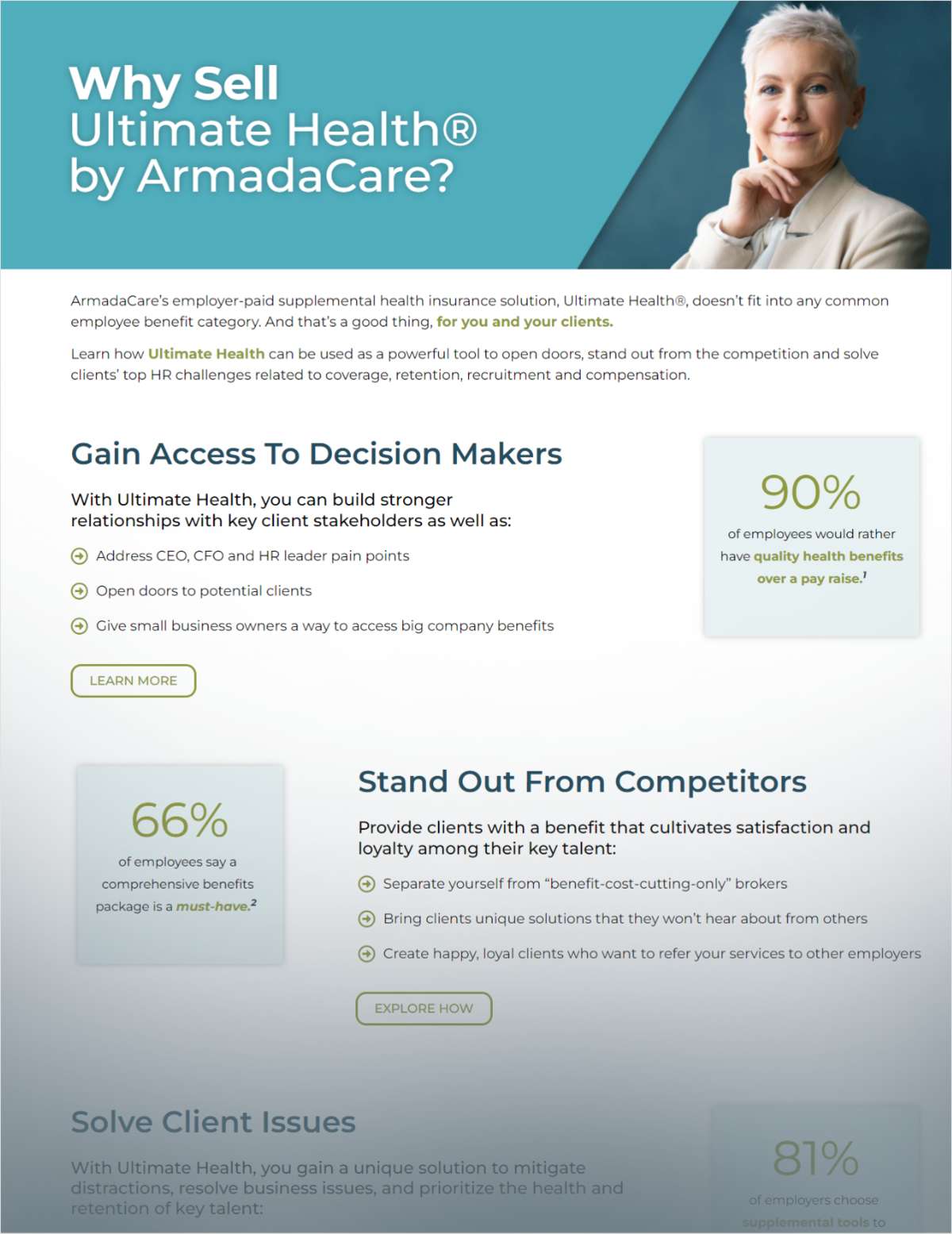
Hackers may have used NSA tools to execute this week’s globalcyberattack, but lawyers say it would be nearly impossible for thevictims, which include law firms, to sue the agency.
|Related: New benefits to help your employeesthrough a data breach
|The attack, which cripped operations at DLA Piper offices inEurope and across the United States, had something in common withthe massive "WannaCry" attack that plagued companies andorganizations last month.
|It appears hackers in both instances executed the attacks byexploiting flaws in Microsoft software originally exposed whentools used by the National Security Agency were hacked and dumpedonline. In a blog postlast month, Microsoft said the leaksillustrate why “stockpiling of vulnerabilities by governments issuch a problem.”
|But some lawyers say it’s not the type of problem DLA Piper, orany other victim, can solve in a courtroom.
|Related: Do investment advisors need a model cybersecurity rule?
|Between the sovereign immunity doctrine, the secretive nature ofthe NSA and the sheer difficulty of proving any guilt on the NSA’spart, suing the agency for allowing its tools to be stolen would bea tough sell.
|“One could file that lawsuit, but whether it would go anywhereis another question,” said Joe Swanson, a former assistant U.S.attorney and of counsel at the firm Carlton Fields.
|The government does face lawsuits over data breaches, but thecontours of those suits are clearer. For example, several classaction lawsuits have been filed against the Office of PersonnelManagement over the massive data breach there, which exposedmillions of federal workers’ personal data. But in those cases, theplaintiffs allege the agency broke the 1974 Privacy Act, whichrequires the government to use certain safeguards to protectrecords kept on individuals.
|In the NSA’s case, records for individuals were not stolen.Rather, it was the agency’s tools or methods that were leaked.
||“A helpful analogy would be like if your neighbor stores a gun,negligently, and a bad guy comes into the house, steals it, andmany months later, uses that gun to harm you,” Swanson said. “So itwould be difficult to recover a negligence claim.”
|Most claims against the government are barred by the sovereignimmunity doctrine. Daniel Girard of Girard Gibbs representsgovernment employees in the data breach lawsuit against OPM pendingin a D.C. federal court. He said that in order to bring a claimagainst the NSA, a plaintiff would need to find a specific waiverof sovereign immunity—a specific instance in which the governmentgave consent to be sued.
|The best option would probably be to file under the Federal TortClaims Act, which allows lawsuits against government employees ifthey cause property damage, injury or death due to negligence or awrongful act. Still, it would be difficult to prove the NSA’snegligence caused any injury or harm, Swanson said.
|Plus, the discovery involved to prove such a claim would likelybe drawn out and expensive since nearly every document a plaintiffmay request from the NSA is probably classified.
|“[The difficulty] is made only worse by the fact that you’d bepursuing one of the most secretive agencies in the country, if notthe world,” Swanson said.
|Swanson added that for victims of the breach, the best option isfor companies to take their own vulnerabilities seriously.
|“The way in which [the malware] operates illustrates the factthat you really cannot be complacent when it comes tocybersecurity,” Swanson said.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.