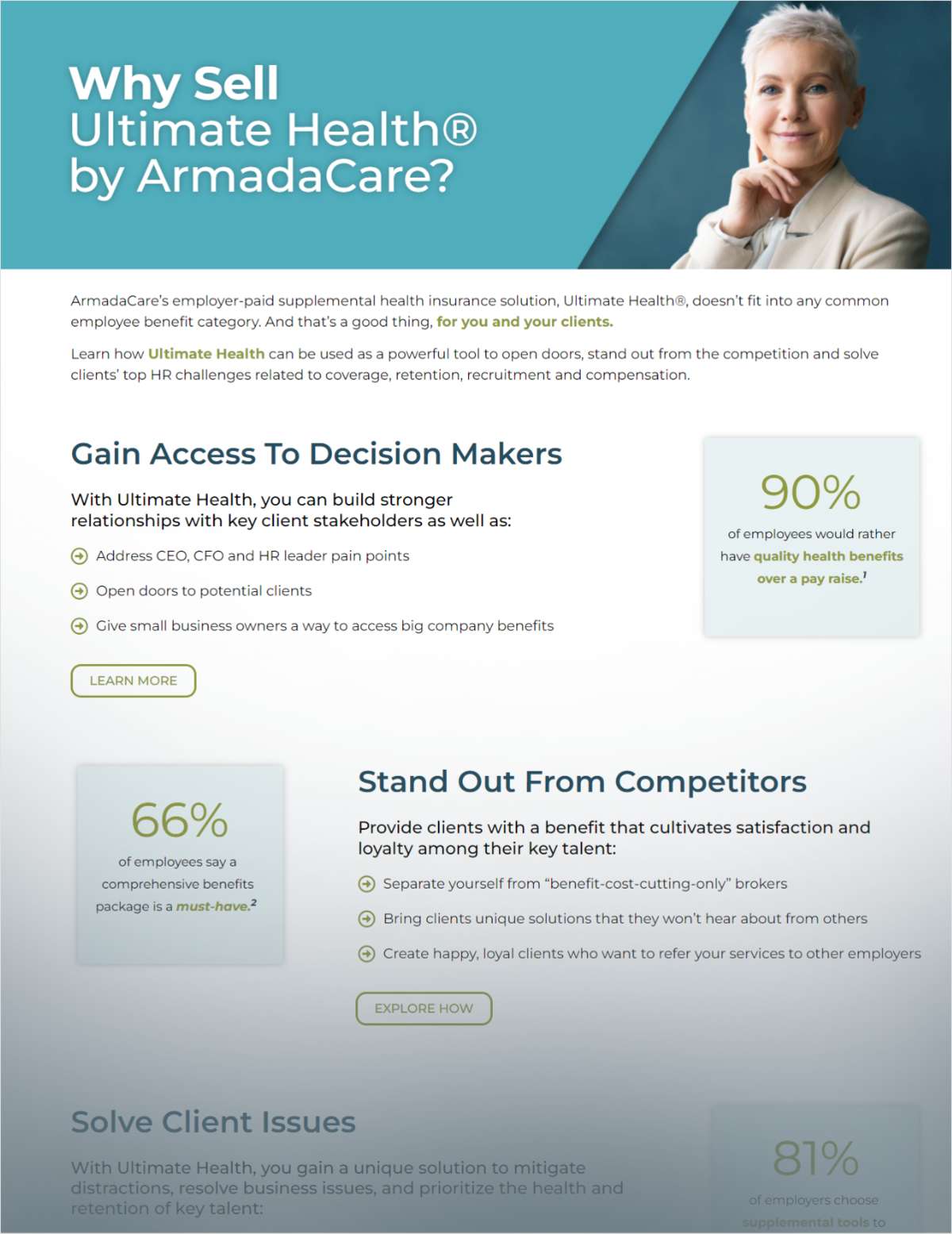
On Oct. 24, the National Association of Insurance Commissioners(NAIC) formally approved the Insurance Data Security Model Law (model law). The NAICis a standard setting and regulatory support organizationconsisting of the top insurance regulators from the 50 states,District of Columbia, and five U.S. territories.
|The model law applies to “licensees” which are defined aspersons and nongovernmental business entities subject tothe insurance laws of the state adopting the model law. InPennsylvania, for example, this would encompass insurance companiesand insurance producers (i.e., agents, agencies and brokers).Notably, this applies to nonresident licensees except forpurchasing groups, risk retention groups or when acting as assuminginsurer. For example, a broker resident in a state that hasnot adopted the model law, is potentially subject to the modellaw if they are also licensed in another state that has adopted themodel law. Thus, it will be important to track what states enactthe model law and also how uniformly the model law is enactedstate to state.
|Related: Cybersecurity and health care: where the concernlies
|The intent of the model law is to establish standards for datasecurity, the investigation of cybersecurity events andnotification of the commissioner of cybersecurity events. In orderto understand how the model law attempts to meet those objectivesit is necessary to understand how the model law has defined thedifferent elements that are involved in cybersecurity. Acybersecurity event is defined as “an event resulting inunauthorized access to, disruption or misuses of, an informationsystem or information stored on such information system.”Information system is defined broadly as “a discrete set ofelectronic information resources organized for the collection,processing, maintenance, use, sharing, dissemination or dispositionof electronic information …” and expressly includes “specializedsystems such as industrial/process controls systems, telephoneswitching and private branch exchange systems, and environmentalcontrol systems.”
|This broad definition encompasses both traditional computernetworks and devices, but also other machines that fall under therubric “the internet of things” and systems such as HVAC systemswhich have been the entry point for hackers in notable databreaches. Information security program means “theadministrative, technical and physical safeguards that a licenseeuses to access, collect, distribute, process, protect, store, use,transmit, dispose of or otherwise handle nonpublicInformation.”
|Nonpublic information is defined more broadly thanmost data breach notification laws and includes business relatedinformation of the licensee the disclosure of which could cause amaterial adverse impact on the licensee’s business, operations orsecurity. Nonpublic information also includes any information abouta consumer which can be used to identify the consumer incombination with any one or more of Social Security number,driver’s license or other identification number, account number,credit or debit card number, security code, access code or passwordto a financial account, or biometric records.
||Nonpublic information also includes any data other than age andgender derived from a health care provider or the consumer relatedto the consumer’s past, present or future physical, mental, orbehavioral health or condition or that of the consumer’s family.Publicly available information means any information thata licensee has a reasonable basis to believe is lawfully madeavailable to the general public from federal, state or localgovernment records; widely distributed media; or, disclosures tothe general public required by federal, state, or local law.
|The model law requires Licensees to implement a comprehensivewritten information security program based on the licensees’ riskassessment. As part of the information security program thelicensee must designate an individual (who can come from a thirdparty) to be responsible for the information security program. Therisk assessment must identify reasonably foreseeable internal andexternal threats to nonpublic information includingany information systems or nonpublic information that arecontrolled or accessible by third-party service providers; assessthe likelihood and severity of damage by these potential threats;assess the sufficiency of existing policies, procedures, andtechnology in place to protect against such threats; and, implementinformation safeguards to manage the identified threats and atleast annually assess their effectiveness. The model law putsspecial emphasis in assessing the licensees’ policies,procedures, information systems and safeguards with respect to:employee training and management; information systemsincluding information classification, governance, processing,storage, transmission and disposal; and, detecting, preventing, andresponding to attacks, intrusions, or other system failures.
|The model law also mandates that Licensees performcontinuing risk management with respect to cybersecurity issues. Alicensee, commensurate with its size and complexity of activities,shall design its information security programs to mitigate therisk identified in the risk assessment. At a minimum alicensee must evaluate the appropriateness of implementing 11enumerated security measures including implementing access controlswith authentication on information systems, restricting access atphysical locations with nonpublic information, encryption and toregularly test and monitor systems and procedures to identifyactual and attempted attacks or intrusions. Licensees must alsoinclude cybersecurity risks in their enterprise risk managementprocess, stay informed regarding emerging threats andvulnerabilities, and provide its personnel with cybersecurityawareness training as necessary to reflect risks identified in therisk assessment.
|The model law also mandates oversight of the informationsecurity program by a licensee’s board of directors, if applicable.Other responsibilities include oversight of third-party serviceproviders, ongoing monitoring, evaluation, and adjustment asnecessary of the information security program, establishment of awritten incident response plan and annual certification ofcompliance with Section 4 to the (insurance) commissioner.
|The model law also contains detailed provisions regarding theinvestigation of and notification regardingcybersecurity events. Licensees must investigate wheneverthere is or may have been a cybersecurity event. The investigationcan be performed by an outside vendor on behalf of the licensee.There are separate notification requirements for the commissioner,consumers and reinsurers. The commissioner also has the authorityto investigate licensees’ compliance with the model law and to takeaction to enforce the model law.
||Importantly, the model law provides forconfidentiality of information provided pursuant to a licensee’sannual certification under Section 4(I) and much of the informationthat must be reported to the commissioner following a cybersecurityevent under Section 6, and investigations under Section 7. Themodel law expressly provides that these documents are not subjectto freedom of information act or similar laws, subpoenas ordiscovery in civil actions and are inadmissible in civil actions.The commissioner is authorized to use such documents as necessaryin any action or proceeding it institutes to enforce the model lawunder Section 7.
|There is an exception for licensees with fewer than 10employees, including independent contractors, and individuallicensees who are covered by the information security program ofanother licensee. In addition, licensees subject to HIPPA that haveestablished and maintain information security programs pursuant toHIPPA are deemed to be in compliance with Section 4. In Section 10the model law contemplates penalties for noncompliance inaccordance with the enacting state’s general penalty statute. Section 11, which is noted as optional allows for theimplementation of additional rules and regulations necessary tocarry out the provisions of the model law.
|The model law is similar, but not identical, in structure andscope to New York’s recent cybersecurity rules applicable to banks,insurance companies and other financial services companies, 23NYCRR 500 (N.Y. cyber rules). The model law contains a draftingnote indicating it is the drafters’ intent that if a licensee is incompliance with the N.Y. cyber rules then the licensee is incompliance with the model law. Like the N.Y. cyber rules the modellaw is based on a risk assessment or risk management approach tocybersecurity. This approach is widely regarded as a best practicein terms of approach to cybersecurity. What is still very much inquestion is the ability of regulations of this type to actuallyimprove cybersecurity. As both the model law and N.Y. cyber rulestacitly acknowledge there is no perfect answer or approach tocybersecurity. Security measures necessary and appropriate forlarge companies will often not fit smaller companies and viceversa. Examples include the frequency and sophistication ofpenetration and other testing methods and the scope and intensityof employee training. Further, it is widely accepted by securityexperts that everybody is vulnerable no matter how rigorous theircybersecurity is. Can regulations effectively improve cybersecurityin this type of risk environment? We shall see.
|Another critical hurdle facing the Model Law that will greatlyimpact how effective it is in improving cybersecurity, is howwidely and uniformly it is adopted by states. These are issues thatoften plague model laws regardless of subject and there arenumerous examples of limited adoption, lack of uniformity ofadoption, or both in existing model laws. Penalties and enforcementare another area that could potentially vary greatly state tostate. The NAIC looks to have come up with a fairly balancedapproach to cybersecurity regulation and companies large and smallwould be wise to follow many of the processes and proceduresrequired by the model law. But there are many open questionssurrounding the model law the answers to which will determine itssuccess at improving cybersecurity in the insurance industry and asa model for other industries to follow.
|Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.