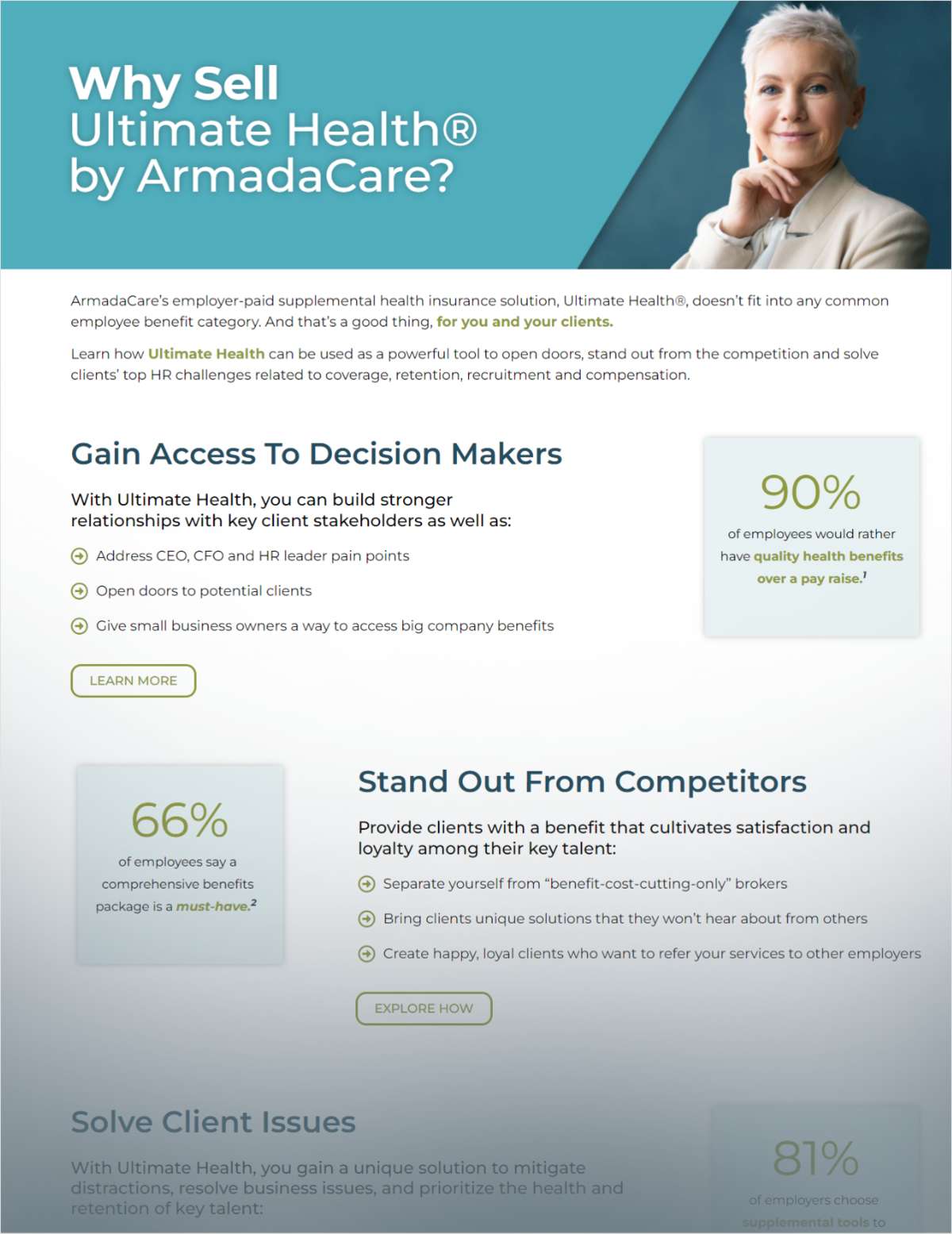
A 2014 breach of Uber'scompany data exposed names and license information for upwards of50,000 current and former drivers.
A 2014 breach of Uber'scompany data exposed names and license information for upwards of50,000 current and former drivers.
|
Managing cybersecurity risk has quickly become one ofthe biggest organizational concerns of the 21st century, especiallywhen that risk is distributed across a number of employees,partners and third-party vendors. But in the new and steadilygrowing gig economy, that risk can be spread far andwide: across thousands, even hundreds of thousands, of contractworkers.
|Eversheds Sutherland partner and U.S. leader of the firm'sglobal cybersecurity and privacy practice Michael Bahar explainedthat for enterprising hackers looking for personalinformation, a gig economy company presents an enormous trove ofvaluable data. “Some of these companies, like the Ubers, theybecome the iconic 'bank.' People know that there's a lot ofpersonal information, both of the driver or the personmoonlighting, as well as their customers,” he said.
|Related: 3 ways HR and benefits managers can mitigatecybersecurity risks
|Indeed, Uber Technologies Inc. has been subject to a barrage ofdata breach attempts, at least one of which exposed the names,email addresses and phone numbers of 57 million Uber users and thedriver's license numbers of at least 600,000 drivers. A 2014 breach of the ride sharing company's data similarlyexposed names and license information for upwards of 50,000 currentand former drivers.
||
But whose fault is it?
Risk of data exposure can be particularly precarious for gigworkers themselves. Recent data collected by Harvard and Columbia University researchers found that many gigeconomy providers often require contractors to upload sensitiveinformation, such as driver's license information, proof ofinsurance and location data, that can put them at serious fraud andsafety risk if exposed.
|The same study found that while companies tend to provide theiremployees with regular cybersecurity training, they often don'textend this training to contract workers, leaving many contractorsrelatively unaware of what they need to do to keep both their ownand company data safe. Malicious hackers seem to have picked up onthis trend, the researchers said, and have begun targeting gigworkers with phishing attacks that can expose their personalinformation.
|Hanson Bridgett attorney Everett Monroe explained that thisdynamic can put companies in a weird place. “The individualcompanies don't have a lot of control, and the independentcontractors don't have a lot of knowledge. You probably want yourgig worker to have better data security, but there's not a lot ofincentive and knowledge for them to build it,” he said.
|One way to deal with this is by creating secured softwarechannels, like an app, for gig workers to interact with companysystems. Indeed, larger companies with broad independentcontractors pools, the Ubers and Lyfts of the gig economy,typically manage contractors remotely, meaning that they often usesimilar kinds of contractor-facing technology as they do withconsumer-facing ones. “Usually they're all going through somemobile platform. So as long as that's secure,” Bahar said,companies should be protected.
|“The trick with contractors and third parties is that if theytouch your network in a meaningful way, that provides a vector ofattack such that if they're not secure, you're not secure,” Baharadded.
|This too can have pitfalls. The research from Harvard andColumbia found that some the ways in which gig economy providersattempted to insure themselves against liability with gig workers,like requiring multiple identity verification, can be easilyemulated and exploited by phishing schemes.
|Bahar noted that for gig economy providers clamoring to be thenext big thing and trying to impress venture funding, consideringthe cybersecurity concerns introduced by a gig-based business modeloften fall secondary to business development. “When you have afirst-to-market approach, you're usually not first-to-security aswell. The more things are the Uber of this and the Uber ofthat—everyone's racing to do that, which is endemic throughout thesystem, that they're not taking cybersecurity first to the system,”he said.
||
The potential legal fallout
Although those filing litigation against gig economy providersfor data breaches haven't been particularly successful thus far,that may not be the case forever. Danielle Urban, partner at Fisher& Phillips, said lawsuits in this area seem to be on the rise.“We've seen more lawsuits. The lawsuits haven't been particularlysuccessful, although they continue to try novel areas of law, and Ithink there will be some inroads,” she said.
|“It's very much unknown terrain legally. You don't want to looklike you have too much control of your contractors,” Urbanadded.
|In many ways, gig economy providers have nearly the sameconcerns and imperatives as your standard company operating intoday's networked landscape. “I don't personally see any specialissues, other than I think that much like employers, I think gigeconomy providers need to realize that their contractors are also avulnerability,” Urban noted.
|Monroe suggested that reframing cybersecurity as a concernlocated within people and the supply chain, rather than technology,can be an important way to go. “The way I would approach this isunderstanding that data security is quite often about how you areworking with humans as opposed to a virus risk or some kind ofadvanced technology threat vectors. When you're keeping that inmind, first a comprehensive data security policy I think is just amust,” he said.
|Urban flagged a few potential things gig economy providers cando to reduce their cybersecurity risk. “There are some bestpractices if you are a gig economy provider. I think you'd want tomake sure that your contracts with contractors specify certainprecautions that they would take,” she said, adding that specifyingwithin contracts what procedures companies plan to take in theevent of a breach can help reduce uncertainty.
|“It's a fine line with gig economy providers, because theyaren't your employees and you don't want to treat them asemployees, but you'd want to make sure that the supply chain is asprotected as it can be,” Urban said.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.