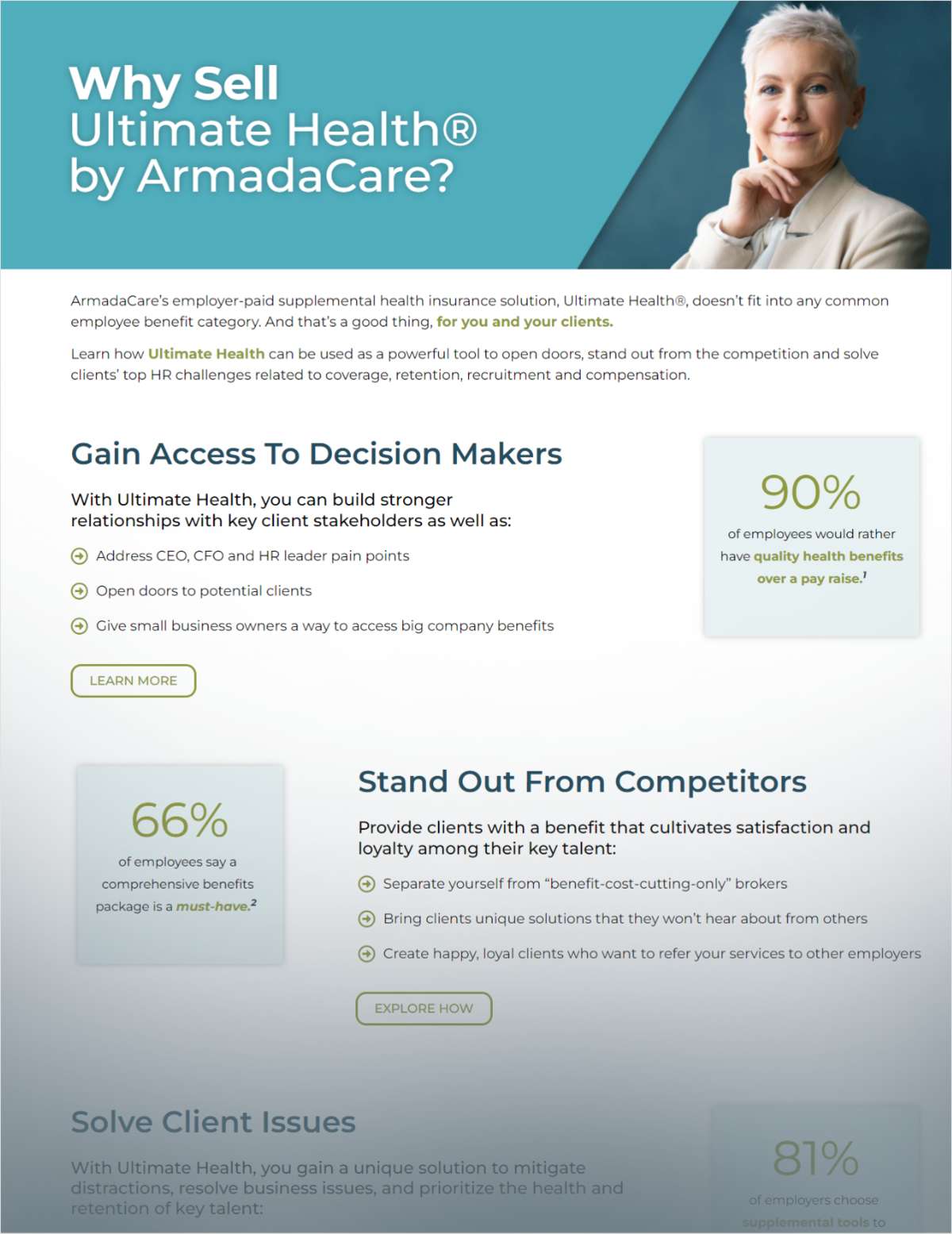
The key to any robust cyber defense strategy involves two things: insight into your own vulnerabilities and insight into evolving adversarial tactics — only then can you truly build defenses that align with evolving enemy strategies. A report by Kroll, a U.S. provider of technology and insights related to risk and governance, claims the threat environment remains complex, and attackers are increasingly targeting email for initial access and extortion.
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.