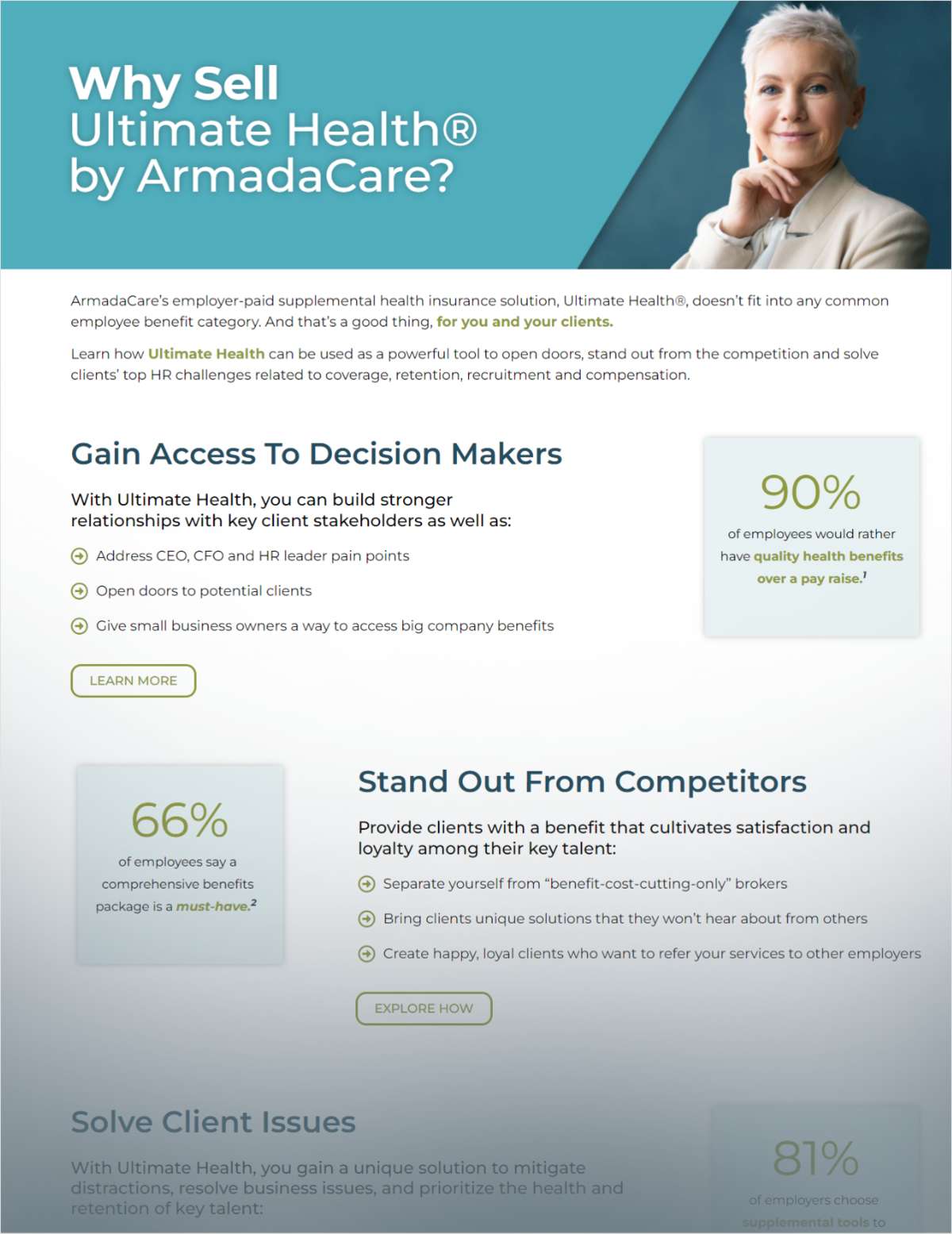
Entreda co-founder and CEO SidYenamandra
Entreda co-founder and CEO SidYenamandra
The top technology concern of advisors andbroker-dealers is cybersecurity, according to polls done by theInvestment Adviser Association and InvestmentAdvisor magazine.
|Addressing this issue are cyber insurers, who work in a marketthat could grow to $17.6 billion in 2023 from about $4.5 billiontoday, Orbis Research says. Driving this growth are factors likedata breaches and the growing use of cloud-based services.
|To look at the risks facing cyber insurers today and thelimitations of this coverage for financial and other firms,ThinkAdvisor spoke at length with Sid Yenamandra, the co-founderand CEO of cybersecurity firm Entreda.
|Yenamandra, who is well-versed in the potential causes of amajor cybersecurity-related disruption, addresses the overallthreat posed to the financial industry by cyber attacks in an earlier interview. In a third (and final)interview, he explains what actions financial firms are and shouldbe taking to improve their cybersecurity.
|ThinkAdvisor: What level of cyber risks do large insurancecompanies have?
|Yenamandra: This is a question thatgoes to the core of what we do as an organization. At Entrada, wework with independent broker-dealers and insurance firms to helpthem manage cybersecurity risk for their firms. We try to assessthe risk holistically within organizations like AIG.
|[Insurance companies do] run the risk of being susceptible to acyberattack, but are they overextended? In the event of a majorattack, I might be overstating it a bit, but I definitely thinkthat big insurance companies have risks.
|There are two points that this brings up. AIG is an underwriterof cybersecurity risk insurance policies for a lot oforganizations.
|Are they overextended in terms of their risk model? Do they havea good way of assessing the risk of an organization before writinga cyber insurance policy for that firm?
|The answer is that today insurance companies are struggling,because there isn't a lot of actuarial science in the area of cyberinsurance. And that's actually a problem the industry is grapplingwith.
|When it comes to auto insurance or home insurance, there areyears and years of data that you can use to build risk modelsaround. But when it comes to cyber, it's been an issue [only] inthe last five to seven years.
|There just isn't a lot of actuarial science around this to helpfirms make better risk decisions, so they're writing insurancepolicies based on self-adaptation from a lot of firms.
|TA: Could you tell more about the risks involved todayin cyber insurance?
|Yenamandra: Firms like AIG are at riskfrom a risk-modelling standpoint. Internally, firms like AIG have anetwork of insurance agents that are writing policies for theirclients.
|There's also a cyber risk … at a corporate level from having anetwork of agents who are independent contractors … in many cases,agents that are running their own business and have their ownoffice locations. They have their own devices, they have their ownnetworks.
|It's like the Wild Wild West, because AIG and other firmsstruggle to manage or supervise cybersecurity risk on the part ofthose 1099 contractors. A large insurance firm might have 5,000-plus reps out in the field.
|They might be spending a fortune on cybersecurity at the homeoffice or the corporate office, but what are they doing at thefringes? How are they helping the small advisor, small insuranceagents or the agency that has five employees, their own devices,their own networks, their own apps in many cases?
|It's unregulated alright.
|There are risks that firms have both from an operationalstandpoint of corporate risk, but also from a product-riskstandpoint around their insurance policy. We think that there is aconsiderable amount of risk — we might not use the phraseoverextended — but I would say they're operating at ahigh level of risk as a business.
|There are also a lot of bad policies out there. Read the fineprint of the exclusions list!
|Firms think, “Yep, we've got insurance, so if we get attackedand we're a victim of cyberterrorism, we're going to get paid outand we're protected.”
|But if you read the fine print, it will say you needed to do thefollowing seven things [to be fully insured]. So the burden ofproof falls on the organization to [show] that it's doing the basicthings when it comes to protecting itself.
|In other words, you can't walk around and have open networks andhope that your insurance policy will cover you. The insurancepolicy is only going to cover you as long as you've taken thenecessary steps to protect yourself.
|And you still may fall victim [to cyberattacks], because thingshappen outside your control. For example, if you getcaught up in a larger cyberterrorism issue — will your policy payout in that case? Again, depends on the policy.
|My point is that cyber insurance or cyber coverage doesn'talways protect you. You've got to pay close attention to the fineprint and work with insurance agents who understand cybersecurity,because then you'll get better advice when it comes to it what thepolicy actually covers.
|TA: Could insurance policies be written without firstensuring that clients are compliant ?
|Yenamandra: It depends totally depend onthe insurance agency.
|A lot of insurance agencies only focus on cybersecurity, andthey probably would do a very good job of making sure they educatethe insureds on what they need to pay attention to.
|But I've seen insurance agencies that are more generalists. Theywrite a lot of insurance policies, but cyber's just another thingthey do. They may not be as educated in that area and therefore maynot be able to provide all of the expertise that a firm has tohave.
|The industry is struggling at a much higher scale with the wayinsurance is currently being written. Today, insurance agents willsend a prospective insured a multi-page application. Thatapplication will have a bunch of questions on it, things like: Doyou have antivirus software on your devices? Do you have backups?Do you have a firewall?
|How do you think a firm is going to respond? If it is trying toget a good policy and a low premium, it's not going to say 'no.' Or[the potential insured] sends it to its [outside] IT firm, whichwill probably say 'yes,' because it's getting paid to do so.
|The problem is that the industry is very much based on selfadaptation.
|The insurance firm gets the self-adaptation model applicationform back from the prospective insured and then it plugs that intoa model, and that model is based on some broad-brushassumptions.
|For example, …. 30% of firms that provide some of that dataaren't going to [provide] correct [information], so they assumethat only 70% of firms are protected. The insurance firm thenwrites a policy based on that [assumption].
|If the organization is as protected as Fort Knox and spends allthis money to protect itself, it's still getting the same policy asa firm that has nothing in place. … The industry today isstruggling with this.
|In the next four or five years, we'll see massive change [with]trust-but-verify models. The insurance agent will have to make surethat a firm is compliant before it gets insurance.
|TA: Could regulators force companies to be insured and to beliable?
|Yenamandra: We're already seeing that if you arean organization that has a lot of power, with power comesresponsibility.
|For example, let's talk about an organization that has [manyindividuals'] Social Security numbers and is operating at a levelthat could put all these people and that data at risk.
|It's certainly within the realm of reason to assume that if [thefirm] does not follow the basics when it comes to cyber risk, thatthe corporate umbrella may be pierced and the CISO may bepersonally liable.
|There is a lot of discussions around [the case of] Equifax. Idon't know if anybody personally was prosecuted, but that casecould be a precedent for a lot of future issues because that attackwas so unprecedented.
|Certain states are mandating that firms have cybersecurityinsurance. And there's been a lot of discussion about holding theCISO of certain organizations personally liable if they're foundnegligent of their fiduciary responsibility.
|READ MORE:
||8 steps to protect employee benefits data fromhackers
|One year later: The influence of Equifax and otherdata breaches on corporate culture
Complete your profile to continue reading and get FREE access to BenefitsPRO, part of your ALM digital membership.
Your access to unlimited BenefitsPRO content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical BenefitsPRO information including cutting edge post-reform success strategies, access to educational webcasts and videos, resources from industry leaders, and informative Newsletters.
- Exclusive discounts on ALM, BenefitsPRO magazine and BenefitsPRO.com events
- Access to other award-winning ALM websites including ThinkAdvisor.com and Law.com
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.